
The SSL Wildcard Certificate can be used to secure an unlimited number of subdomains of a domain. A single wildcard certificate will secure multiple web sites that share the same second-level domain name. For example, if you generate a Wildcard SSL certificate as *.mydomain.com the certificate will secure an unlimited number of subdomains as showed below.
- www.mydomain.com
- blog.mydomain.com
- portal.mydomain.com
- email.mydomain.com
When your SSL certificate expires, the reseller usually sends an email with instructions about renewing your certificate. Renewing an SSL Certificate is the same procedure as obtaining a new SSL Certificate, which means when you renew, it is a requirement to replace your existing SSL Certificate, Private Key and Intermediate CA Certificate within your hosting control panel or server.
In this post I show how to renew an existing SSL Wildcard Certificate with RapidSSLOnline vendor.
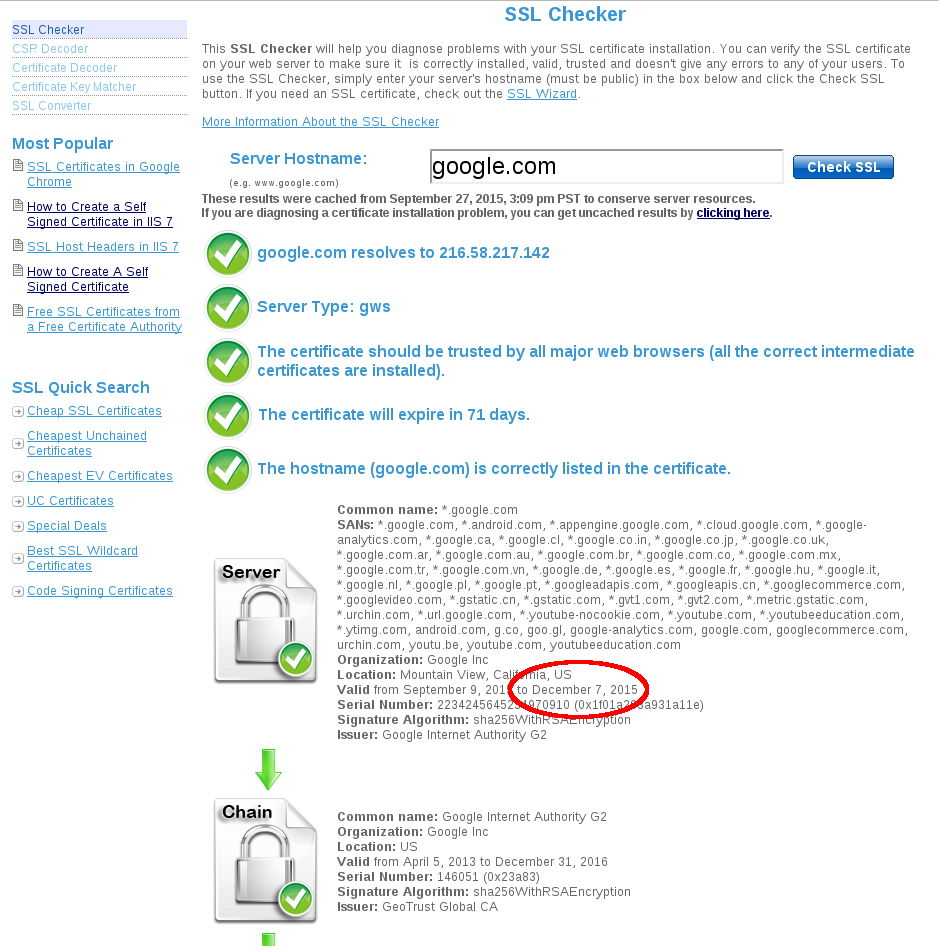
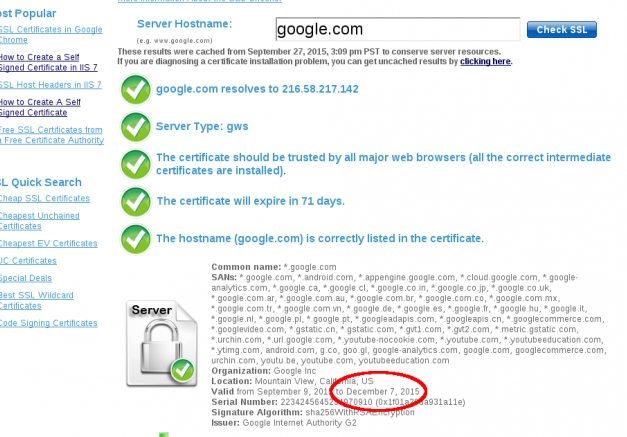
The first thing to do is to check the expiration date of your existing SSL Certificate. You can use a number of online SSL checkers like SSLShopper , Symantec, GeoTrust and so on.
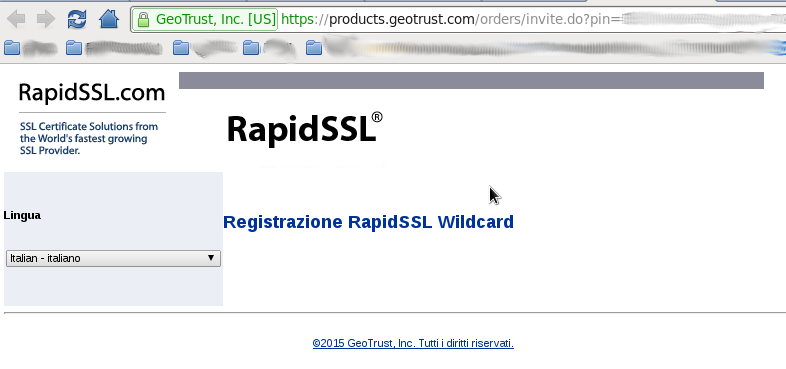
Go to the RapidSSLOnline web site and purchase a wildcard subscription by selecting your desired option of validity.
Once you have made the payment, you will receive an email with a link to complete your order and receive your certificate from the SSL provider. Before proceding with the online ordering system I recommend generating a new Certificate Signing Request and Private Key (avoid using an existing CSR as this will ensure the Private Key will match the new SSL Certificate that is issued).
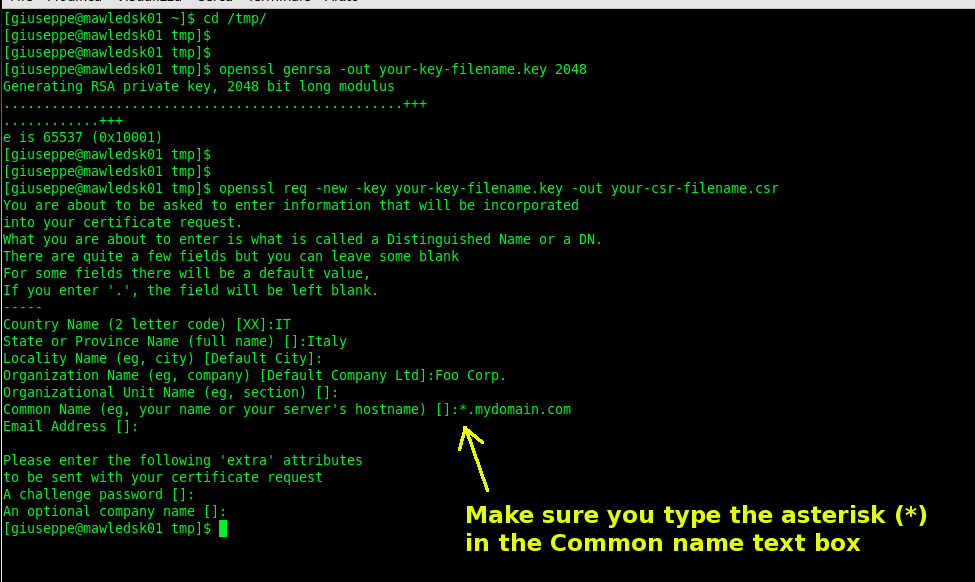
Here is how to generate a new Private Key and CSR for Apache Web Server.(If you have a different Web Server check the list here)
### Generate Private Key ### (In order to bypass the pass phrase requirement I choose to omit the -des3 option) $ openssl genrsa -out your-key-filename.key 2048
### Generate the CSR ### (Do not enter an email address, challenge password or an optional company name when generating the CSR) $ openssl req -new -key your-key-filename.key -out your-csr-filename.csr
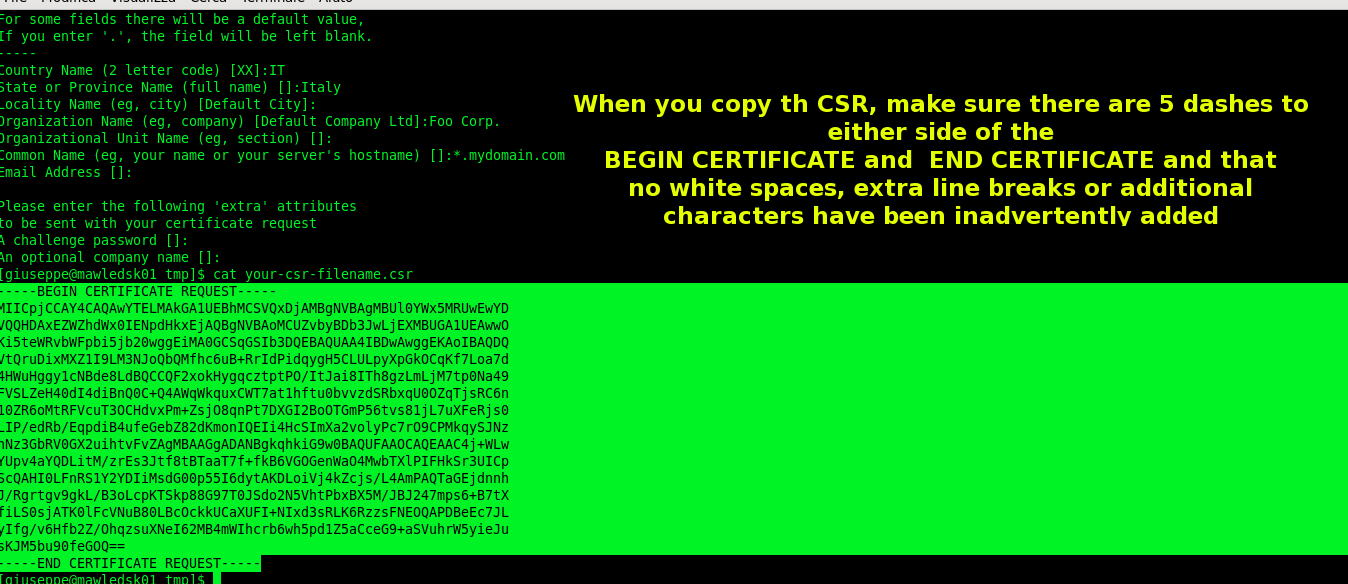
Once you have generated your new Certificate Signing Request you can access the online ordering system and proceede to the renewal options (you’ve received the email with a link after purchasing the new certificate).
### I Use 'cat' command to copy and paste the information into the enrollment online form $ cat your-csr-filename.csr
While you complete the online form, take note of the type of encryption you are using. RapidSSL uses an Intermediate CA to enhance the security of SSL certificates. When installing a RapidSSL certificate, it is essential to install the Intermediate CA at the same time as the SSL certificate. If you choose the SHA-256 encryption into the enrollment online form, you need a RapidSSL SHA-2 (under SHA-2 Root) Intermediate CA Certificate. The RapidSSL and Wildcard certificates Intermediate CA can be downloaded here.
Once the enrollment has been completed, you will receive an Approver email to the designated APPROVER email address selected during enrollment. Unless the Approver receives this email and approves the application by clicking on the link within the email, your certificate cannot be issued. When you click “I APPROVE” the certificate will be issued and emailed to the Applicant, Approver and Technical contact.
The next step is the installation of the new certificate and the intermediate CA on your Server.
### SSL Certificate ### Copy and paste the SSL certificate you've riceived by email after the Approval confirmation. ### (I create a new file) $ vi your-wildcard.crt
### Intermediate CA Certificate ### Copy and paste the contents of the Intermediate CA you've previously downloaded ### (I create a new file) $ vi your-wildcard.intermediate
The final step is the SSL Apache configuration.
### Specify the path for the new SSL Certificate, Private Key and Intermediate CA files $ vi /etc/httpd/conf.d/ssl.conf SSLCertificateFile /opt/secure/your-wildcard.crt SSLCertificateKeyFile /opt/secure/your-key-filename.key SSLCertificateChainFile /opt/secure/your-wildcard.intermediate
### Configure your Apache virtual host $ vi/etc/httpd/conf.d/virtual-hosts.conf ServerName blog.mydomain.com DocumentRoot "/var/www/html/myblog" SSLEngine on SSLProtocol all SSLCertificateFile /opt/secure/your-wildcard.crt SSLCertificateKeyFile /opt/secure/your-key-filename.key SSLCertificateChainFile /opt/secure/your-wildcard.intermediate
### Restart Apache $ /etc/init.d/httpd restart
Once you have installed your SSL Certificate, you can verify that the installation was successful by using one of the above mentioned online SSL Checker.
 English
English Italian
Italian






Thanks for shaing this post…